Privacy

iStock
Zoom video conferencing flaw lets any website hijack your Mac webcam
If you have ever installed Zoom (and even deleted it), any malicious website can access your camera with one click

If you have ever installed Zoom (and even deleted it), any malicious website can access your camera with one click
Any malicious website can force a Mac computer to join a video call with its webcam active, if all the user does is click an innocent-looking link.
This is the result of a zero day vulnerability discovered in the Mac version of the Zoom video conferencing application. Unearthed and made public by security researcher Jonathan Leitschuh, the flaw even continues to work if the user uninstalls Zoom from their Mac.
Read More:
Zoom claimed to have 40 million users back in 2010, and as Macs represent 10 percent of the computer market, we can conservatively estimate that this vulnerability puts four million people at risk of their webcam being hijacked. Zoom's corporate customers include Uber, Slack, Logitech, Caesars Entertainment, Dropbox, Nasdaq, Box, WesternUnion and GoDaddy.
Writing in a Medium blog post, Leitschuh explains how he first contacted Zoom about the serious vulnerability in March, and gave it the industry-standard 90 days to come up with a fix. Because this did not happen, Leitschuh went public about his findings, warning Zoom users about the problem.

The vulnerability centers around what Zoom describes as a unique benefit of its video conferencing system over all others - how you can join a video conference with one click.
This is indeed useful, and means you don't even need to create a Zoom account to access your host's conference call. However, this simplicity has significant consequences.
Firstly, Leitschuh demonstrates in his post how it is possible to throw a visitor to any website into a video call by having them click a link. This link could be dressed up as something else, like an advert or something attractive the website visitor might want to click on. "This could be embedded in malicious ads, or it could be used as a part of a phishing campaign," Leitschuh pointed out.
Once they click, the video call will be opened and their camera will be switched on. The issue here is that the host of the meeting - the person running a malicious website, for example - can set it up in such a way that participants' cameras are automatically switched on when they join the meeting.
GearBrain can confirm that this still works. We clicked a link provided in Leitschuh's blog post and were dropped into a video call with others wondering what was going on. Leitschuh reinforced: "It's important to note that the default configuration for Zoom is to allow a host to choose whether or not your camera is enabled or not by default."
Zoom fixed this inside the 90-day limit, disabling the host's ability to switch on participants' cameras. But on June 7 there was a regression in the fix, allowing the vulnerability to be exploited again.
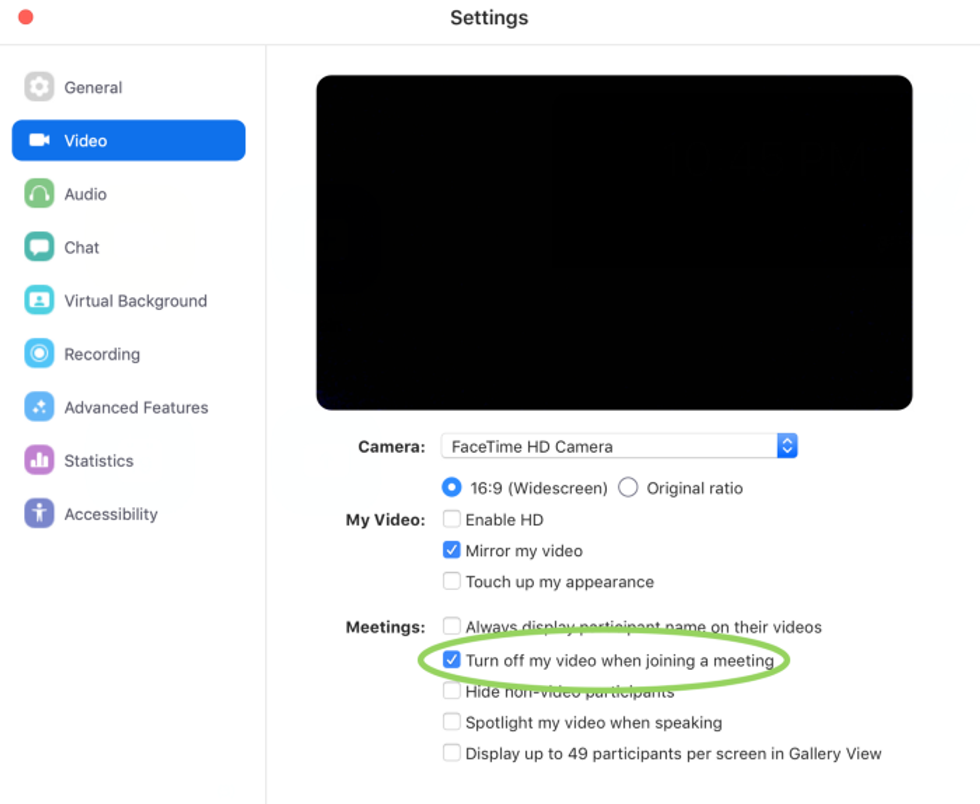
Users are urged to go into the Zoom settings menu and enable the checkbox for 'turn off my video when joining a meeting'.
The second issue raised by Leitschuh is how Zoom installs a web server on your Mac when you download the application for the first time. Then, even if you later uninstall and delete Zoom, the web server remains in place so that when you click a Zoom link, the app is automatically reinstalled without the user's control. GearBrain also confirmed this is the case, with the Zoom app reinstalling itself when we clicked on the video conference link provided by Leitschuh.
This web server can be deleted, but only by entering some commands into the Terminal app of your Mac; Leitschuh explains what to do at the end of his article.
Leitschuh said: "Having an installed app that is running a web server on my local machine with a totally undocumented API feels incredibly sketchy to me...Secondly, the fact that any website that I visit can interact with this web server running on my machine is a huge red flag for me as a security researcher."
He added that this setup is like "painting a huge target on the back of Zoom".
GearBrain Compatibility Find Engine
A pioneering recommendation platform where you can research,
discover, buy, and learn how to connect and optimize smart devices.
Join our community! Ask and answer questions about smart devices and save yours in My Gear.
