Data Protection

iStock
IoT Devices Protection: Must-Dos for the Owner
Safeguarding Your Smart Home: Essential Tips for IoT Security

Safeguarding Your Smart Home: Essential Tips for IoT Security
While still not universal, the Internet of Things is inevitably creating a place for itself in our homes, jobs, hospitals, and collective consciousness. It's pushing the boundaries of interconnectedness, allowing for fine control of climate, lighting, power, entertainment, and more with a few spoken words.
As exciting as the prospect of having your own little IoT empire is, the technology comes with privacy and security challenges you need to be aware of. This article brings several must-know tips on IoT device cybersecurity. It will guide your purchasing decisions and highlight the best security practices for existing devices, so we encourage you to take everything in!

The IoT industry is growing at an explosive rate, with valuation projections of $1.4 trillion for 2024 alone. Household names and newcomers battle it out, and there are more choices in the most popular categories than ever. It makes purchasing a suitable IoT device more challenging. However, you should thoroughly research each new purchase to have as few regrets and complications as possible. Here's what to consider.
Before pulling the trigger on any IoT device, "Do I need this?" is the first thing you should ask. Gadgets like smart thermostats, doorbells, and lights make life more convenient. On the other hand, how useful is a washing machine whose only "smart" feature is sending a notification once the laundry's ready?
Every IoT gadget represents another potential entry point for hackers and snoops. You may be able to find some opt-out guides for specific personal data, but not things like the breached video content filmed at your house. Limiting yourself to genuinely impactful ones will keep the likelihood of attack low.

Personalization and customization are big IoT selling points. They also presuppose a user's willingness to create an account and supply data. The manufacturers openly or covertly collect and store data on anything from your sleeping or nutrition habits to your political views or videos taken inside your home. That's on top of all the personal and financial information accounts or subscription plans require.
Before buying, ensure the manufacturer has a transparent data collection policy and safeguards that protect that data from breaches. You should also check if they were involved in past breaches or sold customer data to others.

Always keeping the drivers updated is a core cybersecurity tip for any device. However, you can only do so if the manufacturer bothers to put updates out! It's common for shady ones to release a product without long-term support. That's problematic since the older the firmware is, the greater the chance someone will detect and exploit its vulnerabilities.
Consider a company's reputation and reviews from long-term users when purchasing new IoT devices. Sometimes, that means going with a more expensive product. Investing in quality now is infinitely better than dealing with the consequences.
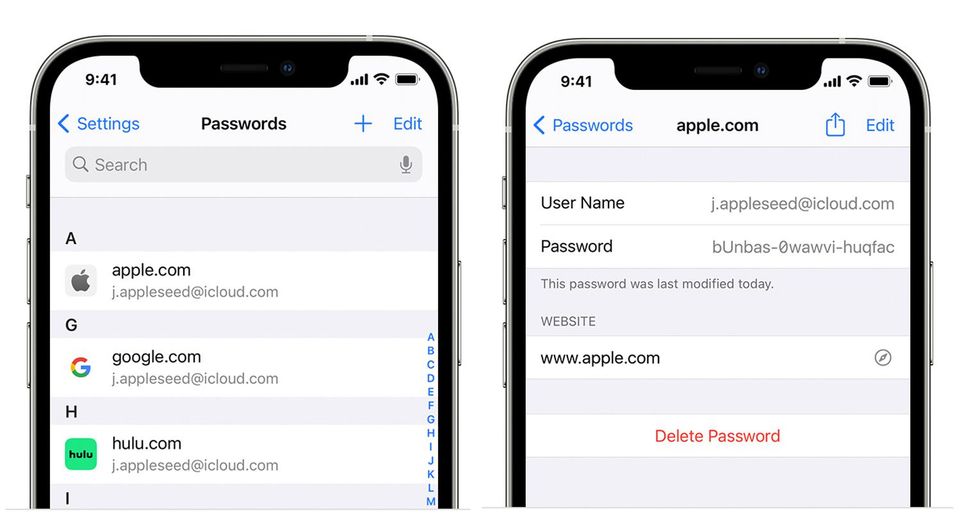
Connecting most smart gadgets to your home network couldn't be easier. Most users leave it at that, not realizing the dangers such carelessness can bring. Put the following tips into practice to use your new devices safely.
Most IoT gadgets require an account to use all the features. Some may not need an online account but still have usernames and passwords for identification. Too many owners will leave the defaults, giving anyone who bothers to look those up access. The more devices you have, the worse the problem becomes.
Building your smart home is the perfect opportunity to start using a password manager. They're convenient because they store all your passwords in an encrypted vault accessible from your computer or phone. Moreover, they can generate strong, distinctive passwords for all smart devices and any accounts you want to set up for family members.
Managing interconnected IoT gadgets becomes increasingly challenging with every addition. Each should have a recognizable and sensible name for easy recognition, especially for gadgets you're likely to have more of, like smart bulbs and plugs.
There also needs to be a way for you to prove ownership. Some devices will have apps that take advantage of your phone's biometrics and authenticate you via fingerprint or face identification. Implementing such protections is essential even if they aren't a regular feature. Conveniently, password managers often incorporate two-factor authentication, which you can use to link IoT accounts to a smartphone or authentication app.
Connectivity is IoT's defining feature. Devices talk to each other and send info back to the manufacturer, making them alluring attack targets. While cutting the connection would render them valid, you can still limit their interactions with the rest of your network through segmentation.
This security strategy isolates IoT devices from others and assigns them to a separate subnet. The advantages are twofold. On the one hand, segmentation limits vulnerability-induced cyberattacks from spreading past the contained subnet and affecting more essential parts of the network. Conversely, it lets you monitor that subnet's traffic more closely and react sooner if you notice an unusual increase.
The Internet of Things is ushering in a new age in which devices work harmoniously to make our lives easier and more fulfilling. Realizing the associated risks and setting up proper precautions will let you experience all of the smart home's advantages while keeping drawbacks and cybersecurity concerns to a minimum.
GearBrain Compatibility Find Engine
A pioneering recommendation platform where you can research,
discover, buy, and learn how to connect and optimize smart devices.
Join our community! Ask and answer questions about smart devices and save yours in My Gear.
