The Internet of Things (IoT) has become ubiquitous, with billions of connected devices being used worldwide. These devices offer unprecedented convenience and automation, from smart home appliances to industrial sensors. However, this connectivity also opens up new vulnerabilities and risks, as hackers can exploit weaknesses in IoT devices to gain access to sensitive data or control systems remotely. This article will discuss the best practices and tips for securing your IoT devices and protecting your privacy and data.
Table of Contents
Content
Introduction
- Understand the Risks
- Keep Your Devices Up-to-Date
- Use Strong and Unique Passwords
- Secure Your Network
- Disable Unnecessary Features
- Monitor Your Devices
- Use a Virtual Private Network (VPN)
- Consider Using a Firewall
- Be Careful About What You Connect
- Use Two-Factor Authentication
FAQs
Conclusion
Introduction
As we rely more and more on technology, it's increasingly important to take steps to secure our devices against cyber threats. This is especially true for IoT devices, which are often connected to the internet 24/7 and may need more security measures. By following these best practices and tips, you can help protect your privacy and data from prying eyes and keep your devices safe from hackers.
Understand the Risks
Understanding the risks is an essential first step in securing your IoT devices. IoT devices are vulnerable to various security threats, including hacking, malware, and data breaches. By understanding these risks, you can take steps to protect your devices and prevent potential security breaches.
Here are some best practices to follow when it comes to understanding the risks of IoT devices:
- Research your device before purchasing: Before purchasing an IoT device, research the manufacturer's security practices and check for any reported security vulnerabilities. This can help you make an informed decision about the security risks associated with the device.
- Understand how your device works: Make sure to understand how your IoT device works, including how it communicates with other devices and the internet. This can help you identify potential vulnerabilities and take steps to protect your device.
- Be aware of common attack methods: Educate yourself about common attack methods used by hackers and cybercriminals, such as phishing scams and malware. This can help you identify potential threats and take steps to prevent them.
- Use strong and unique passwords: Always use strong and unique passwords for all your devices and accounts. This can help prevent unauthorized access and protect your devices from potential security breaches.
- Regularly update your device: Regularly update your IoT devices with the latest firmware updates and security patches. This can help protect your devices from the latest security threats and vulnerabilities.
By understanding the risks associated with IoT devices, you can take steps to protect your devices and prevent potential security breaches. Always research your devices before purchasing, use strong and unique passwords, and regularly update them to protect them from the latest security threats.
Keep Your Devices Up-to-Date
Keeping your IoT devices up-to-date is vital in securing them from potential security breaches. Manufacturers often release software updates and security patches to address known vulnerabilities and protect devices from new security threats. Not updating your devices can make them vulnerable to cyber-attacks and data breaches. Here are some best practices to follow when it comes to keeping your IoT devices up-to-date:
- Enable automatic updates: Most IoT devices have the option to enable automatic updates. Enabling this feature ensures that your devices will receive the latest software updates and security patches as soon as they become available.
- Check for updates regularly: If your device does not support automatic updates, check for updates regularly. Manufacturers often release updates to address known vulnerabilities and security threats, so checking for updates periodically can help ensure that your devices are protected.
- Update all connected devices: Make sure to update all your connected IoT devices, including smart home devices, security cameras, and other connected devices. Even if one device is left un-updated, it can leave your entire network vulnerable to potential security breaches.
- Keep your router up-to-date: Your router is the central point of your home network, and it's essential to keep it up-to-date with the latest firmware updates and security patches. This can help protect your entire network from potential security threats.
- Replace outdated devices: If your IoT device is no longer receiving software updates and security patches, it's time to replace it with a newer device supported by the manufacturer. Out-dated devices are more vulnerable to security threats and can leave your network at risk.
By keeping your IoT devices up-to-date, you can help protect them from potential security breaches and ensure they continue functioning correctly. Enabling automatic updates, checking for updates regularly, updating all connected devices, keeping your router up-to-date, and replacing outdated devices are all important steps in keeping your devices secure.
Use Strong and Unique Passwords
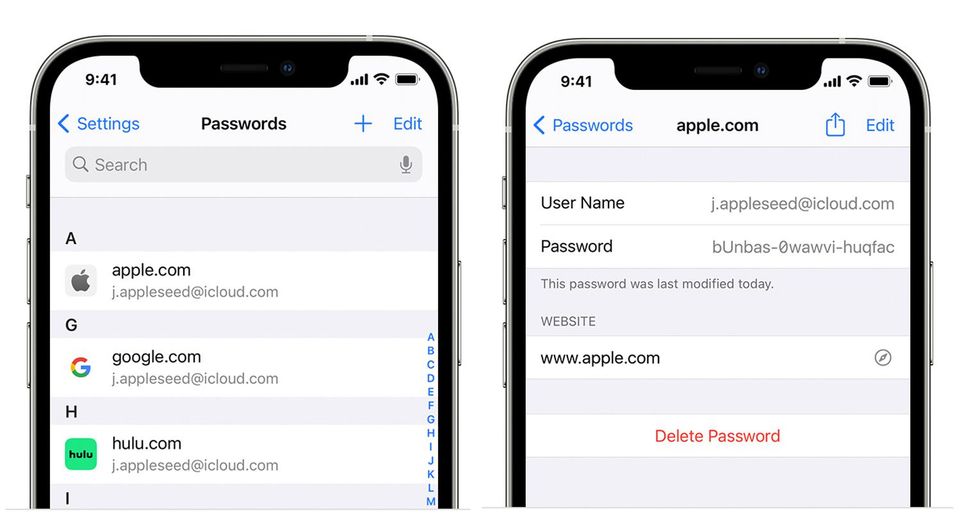
 Viewing passwords saved on an iPhone
Apple
Viewing passwords saved on an iPhone
Apple
Using strong and unique passwords is vital in securing your IoT devices. Default passwords that come with IoT devices are often weak and easily guessable, which makes them vulnerable to cyber-attacks. Using strong and unique passwords to protect your devices and personal data is essential.
Here are some best practices to follow when it comes to creating strong and unique passwords:
- Use a mix of letters, numbers, and symbols: Combining upper and lower case letters, numbers, and symbols can make your password more secure and difficult to guess.
- Avoid using common words and phrases: Avoid using common words and phrases that can be easily guessed, such as "password" or "123456". Instead, use a combination of random words unrelated to each other.
- Create long passwords: The longer your password, the more difficult it is to crack. Aim for a password that is at least 12 characters long.
- Use a password manager: A password manager can help you generate and store strong and unique passwords for all your IoT devices. This eliminates the need to remember multiple passwords and ensures each password is unique and difficult to guess.
- Change your passwords regularly: Changing your passwords regularly can help prevent unauthorized access to your IoT devices. Aim to change your passwords every 3-6 months.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security to your IoT devices by requiring a second form of authentication in addition to your password. This can include a fingerprint scan, a code sent to your mobile device, or a security key.
By using strong and unique passwords, you can help protect your IoT devices from potential security breaches and ensure your personal data remains secure.
Secure Your Network
 Secure your network with essential steps iStock
Secure your network with essential steps iStock
Securing your network is an essential step in securing your IoT devices. Your network is the foundation for all your IoT devices and can be vulnerable to attacks if improperly secured.
To secure your network, consider implementing the following best practices:
- Please change the default password: The default password on your router may be easy to guess, making it vulnerable to attacks. Change the default password to a strong, unique password to secure your network.
- Use strong encryption: Ensure your network is encrypted with a strong encryption protocol like WPA2. This can help protect your network from potential attacks and prevent unauthorized access.
- Separate your network: Consider separating your IoT devices from your main network by creating a separate guest network. This can help prevent unauthorized access to your main network if an IoT device is compromised.
- Update your router firmware: Regularly check for and install any available updates for your router firmware. These updates often include critical security fixes that address vulnerabilities and protect your network from potential attacks.
- Use a firewall: Enable a firewall on your router to block unauthorized access to your network and prevent potential attacks.
- Disable remote management: Disabling remote management can prevent unauthorized access to your router and protect your network from attacks.
- Monitor your network: Regularly monitor your network for any unusual activity or devices you do not recognize. This can help detect potential attacks and prevent unauthorized access to your network.
Securing your network can help protect your IoT devices and personal information from attacks. Network security is critical to IoT security and should be considered an essential best practice for any IoT device owner.
Disable Unnecessary Features
Disabling unnecessary features is a critical best practice when securing your IoT devices. IoT devices often come with various features and settings, some of which may be optional for your specific use case. These features can introduce new security risks and vulnerabilities to your device, so it's essential to disable any unnecessary. Here are some best practices to follow when disabling unnecessary features:
- Identify and review all device features: Identify your device's features and settings. Review each one carefully and determine whether it's necessary for your use case.
- Disable unused features: If you come across any features that are not necessary, disable them immediately. This includes remote access, file sharing, or automatic firmware updates.
- Limit user permissions: Limit user permissions to only what is necessary for their specific use case. This can help prevent unauthorized access and reduce the risk of a compromised device.
- Keep your device up-to-date: Regularly update your device with the latest firmware updates and security patches. This will help protect your device from the latest security threats.
- Review and update device settings regularly: Regularly review and update your settings to ensure you use the most secure configuration possible.
By disabling unnecessary features, you can help reduce the attack surface of your IoT devices and protect them from potential threats. Always review and disable any features that are not necessary for your specific use case, and make sure to keep your devices up-to-date with the latest security patches and firmware updates.
Monitor Your Devices
 IoT devices need digital security
iStock
IoT devices need digital security
iStock
Monitoring your IoT devices is an essential step in securing them. Regular monitoring can help detect any unusual activity or potential attacks and allow you to take action to prevent them.
To monitor your devices, consider implementing the following best practices:
- Please keep track of your devices: Keep a record of all the IoT devices you own, along with their IP addresses, MAC addresses, and other identifying information. This can help you detect any unauthorized devices on your network and allow you to take action to remove them.
- Use network monitoring tools: Use network monitoring tools to monitor your network traffic and detect any unusual activity. These tools can help you identify potential attacks and allow you to take action to prevent them.
- Enable logging: Logging on your IoT devices to track changes or activity. This can help you detect any unauthorized access and allow you to take action to prevent further damage.
- Regularly check for firmware updates: Regularly check for your IoT devices and install them as soon as possible. These updates often include critical security fixes that address vulnerabilities and protect your devices from potential attacks.
- Check for unusual behavior: Regularly check your devices for any unusual behavior or activity. This can include unexpected changes in device settings, unusual network traffic, or unauthorized access attempts.
- Use antivirus software: Install antivirus software on your devices to detect and remove any malware that may be present. This can help protect your devices and personal information from potential attacks.
By monitoring your IoT devices regularly, you can help detect any potential attacks and take action to prevent them. Monitoring your devices should be considered an essential best practice for any IoT device owner.
Use a Virtual Private Network (VPN)
A Virtual Private Network (VPN) is vital in securing your IoT devices. A VPN creates a secure, encrypted connection between your device and the internet, making it difficult for attackers to intercept your data or monitor your online activities.
Here are some best practices to follow when using a VPN with your IoT devices:
- Choose a reputable VPN provider: It's important to choose a VPN provider with a good reputation and a proven track record of providing reliable and secure services. Look for a provider with strong encryption protocols and a no-logging policy.
- Install the VPN software on all your devices: Make sure to install the VPN software on all your IoT devices that connect to the internet. This will help protect all your online activities, even if you switch between devices.
- Use a dedicated VPN router: Consider using a dedicated one for your IoT devices. This can help ensure the VPN protects all your devices, even if they don't support VPN software.
- Keep your VPN software up-to-date: Make sure to keep your VPN software up-to-date with the latest security patches and updates. This will help ensure that your VPN always provides the best possible protection for your devices.
- Use a strong, unique password: When setting up your VPN, use a strong, unique password. This will help prevent unauthorized access to your VPN account and ensure your data remains secure.
- Avoid free VPN services: While many are available, avoiding them is generally best. Free VPNs often have limited features and may provide a different level of security than paid VPN services.
VPN with your IoT devices, you can help protect your online activities and data from potential attackers. A VPN should be considered an essential best practice for securing IoT devices.
Consider Using a Firewall
Consider using a firewall to protect your IoT devices from potential threats. A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.
Here are some best practices to follow when using a firewall to secure your IoT devices:
- Choose a reputable firewall solution: Many hardware and software-based firewall solutions are available. Choose a reputable firewall solution that meets your needs and has a proven track record of providing reliable and effective security.
- Configure your firewall correctly: Make sure to configure your firewall correctly according to the manufacturer's instructions. This may include setting up rules to block incoming traffic, allowing only authorized traffic, and monitoring network traffic for suspicious activity.
- Enable port forwarding only when necessary: Port forwarding can be helpful in certain applications, but it can also create security vulnerabilities if not configured correctly. Only enable port forwarding when necessary, and make sure to configure it correctly.
- Keep your firewall up-to-date: Keep your firewall software up-to-date with the latest security patches and updates. This will help ensure that your firewall provides the best protection for your devices.
- Use a strong, unique password: When setting up your firewall, use a strong, unique password. This will help prevent unauthorized access to your firewall and ensure your network remains secure.
- Regularly monitor your firewall logs: Regularly monitor your firewall logs to detect any unusual activity. This can help you identify potential attacks and take action to prevent them.
Firewalls will protect your IoT devices; you can help prevent unauthorized access and protect your devices from potential threats. A firewall should be considered an essential best practice for securing IoT devices.
Be Careful What You Connect
One important best practice to remember when securing your IoT devices is to be careful what you connect to your network. Every device you connect to your network has the potential to introduce new security risks and vulnerabilities.
Here are some best practices to follow when connecting devices to your network:
- Only connect devices from reputable manufacturers: When purchasing new IoT devices, only buy them from reputable manufacturers with a track record of producing secure and reliable products.
- Research devices before you buy them: Before purchasing a new IoT device, research to ensure it has good security features and a proven track record.
- Only connect devices that you need: Only connect devices to your network that you actually need. The more devices you have connected to your network, the more potential security risks you introduce.
- Only connect devices that are supported: If a device no longer receives security updates or support from the manufacturer, it's best not to connect it to your network. This can leave your network vulnerable to attacks.
- Use a separate network for IoT devices: Consider setting up a different network for your IoT devices. This can help isolate them from your main network and reduce the risk of a compromised device affecting other devices on your network.
- Regularly update device firmware: Keep your devices up-to-date with the latest updates and security patches. This will help protect your devices from the latest security threats.
By being careful about what devices you connect to your network, you can help reduce the risk of a security breach and protect your IoT devices from potential threats. Always take the time to research devices before you buy them, and regularly update them with the latest security patches to stay protected.
Use Two-Factor Authentication
Using two-factor authentication is a critical best practice when securing your IoT devices. Two-factor authentication (2FA) is an additional layer of security that requires users to provide two forms of identification before being granted access to a device or system.
Here are some best practices to follow when using two-factor authentication to secure your IoT devices:
- Choose a reputable 2FA solution: There are many 2FA solutions available, including hardware tokens, software tokens, and biometric authentication. Choose a reputable 2FA solution that meets your needs and has a proven track record of providing reliable and effective security.
- Enable 2FA on all devices that support it: Many IoT devices support 2FA, but it may not be enabled by default. Make sure to enable 2FA on all devices that support it to provide an additional layer of security.
- Use a strong, unique password: When setting up 2FA, use a strong, unique password. This will help prevent unauthorized access to your device and ensure your network remains secure.
- Don't reuse passwords: Don't reuse passwords across multiple devices or accounts. If a password is compromised, it can be used to access other devices or accounts.
- Regularly update your password: Regularly update your 2FA password to help prevent unauthorized access to your devices.
Using two-factor authentication to secure your IoT devices, you can help prevent unauthorized access and protect your devices from threats. Using 2FA should be considered an essential best practice for securing IoT devices.
FAQs
Q: How can I tell if my IoT device has been hacked?
A: Signs that your IoT device has been hacked may include unusual activity, such as data transfers or reboots, or changes to your device settings. Additionally, if you notice any suspicious behavior, such as your camera or microphone turning on unexpectedly, it may be a sign that your device has been compromised.
Q: Can I secure my IoT devices using antivirus software?
A: While antivirus software can help protect against certain types of malware, more is needed to secure your IoT devices fully. This is because IoT devices often have limited processing power and may be unable to run resource-intensive security software. Instead, focus on other best practices, such as keeping your devices up-to-date and using strong passwords.
Q: What should I do if I suspect my IoT device has been hacked?
A: If you suspect your IoT device has been hacked, immediately disconnect it from the internet and contact the manufacturer for support. Additionally, consider changing your passwords and monitoring your other devices for signs of compromise.
Q: Can I still use my IoT devices if I disable certain features?
A: Yes, in most cases, you can still use your IoT devices even if you disable certain features. However, be aware that some features may be necessary for specific functions or for the device to work properly.
Q: How often should I update my IoT devices?
A: It's a good idea to regularly check for updates for your IoT devices, such as once a month. Many manufacturers release security patches and firmware updates to address known vulnerabilities or improve device performance. Keeping your devices up-to-date can help reduce the risk of cyber-attacks and keep your devices running smoothly.
Q: What should I do if the manufacturer no longer supports my IoT device?
A: If the manufacturer no longer supports your IoT device, consider replacing it with a newer model. Unsupported devices may not receive security updates or patches, making them more vulnerable to cyber-attacks.
Q: Can I use the same password for all my IoT devices?
A: Using the same password for all your IoT devices is not recommended, as this can increase the risk of a widespread compromise if one password is compromised. Instead, use unique, strong passwords for each device and consider using a password manager to keep track of them.
Q: How can I protect my IoT devices from physical attacks?
A: Physical attacks, such as theft or tampering, can also pose a risk to your IoT devices. To protect against physical attacks, consider installing your devices in secure locations or using anti-tampering features, such as locks or tamper-evident seals.
Q: What are some common IoT vulnerabilities to be aware of?
A: Some common IoT vulnerabilities include weak or default passwords, unsecured communication protocols, and outdated software or firmware. Additionally, many IoT devices may need better security practices, such as using unencrypted data storage or transmitting sensitive data without encryption.
Q: How can I ensure that my IoT devices are GDPR-compliant?
A: If you are using IoT devices to collect or process personal data, it's important to ensure that you comply with the General Data Protection Regulation (GDPR). This may involve implementing security measures to protect personal data, obtaining user consent, and providing transparency about data use.
Conclusion
Securing your IoT devices is critical in protecting your privacy and preventing cyber-attacks. By following best practices such as disabling unnecessary components, monitoring your devices, and using strong passwords, you can help reduce the risk of compromise and keep your devices running smoothly. Additionally, staying up-to-date on the latest security threats and vulnerabilities is essential as taking steps to protect your devices accordingly. With these tips and best practices in mind, you can enjoy the benefits of IoT technology while keeping your devices and data safe and secure.
Author bio
Eric Spin is a content marketer at Averickmedia with four years of experience. He employs his knowledge in content strategy, SEO optimization, social media management, and data analysis to help his clients' websites receive more traffic, convert customers, and establish their brands. To engage and inform the audience, he has developed his ability to create intriguing storylines and offer high-quality material.
From Your Site Articles
Related Articles Around the Web