Hackers

iStock
Google discovers malicious websites injecting iPhones with 'monitoring implants' for years
Researchers reveal websites have been indiscriminately targeting iPhone users through 12 security flaws.

Researchers reveal websites have been indiscriminately targeting iPhone users through 12 security flaws.
Malicious websites running for at least two years and visited by thousands of victims every week contained software designed to attack iPhones.
This is the finding of cybersecurity researchers working for Google's Project Zero division, who discovered the websites in January 2019. Apple has since fixed the iPhone flaws, but not for every handset, as older models cannot run iOS 12.
Read More:
The iPhone 5 is the most recent iPhone to not get upgraded to iOS 12 (and won't get iOS 13 either). It, as well as the iPhone 5C, 4S and all older devices, of which some are still in use, will remain vulnerable to the malware discovered by Google, as they still run iOS 11 or older.
Before the fix, which was issued by Apple with iOS version 12.1.4 on February 7, the websites attacked every iPhone which visited them. Users did not have to interact with the website in any way, or download anything; simply visiting them was enough to cause harm to their device.
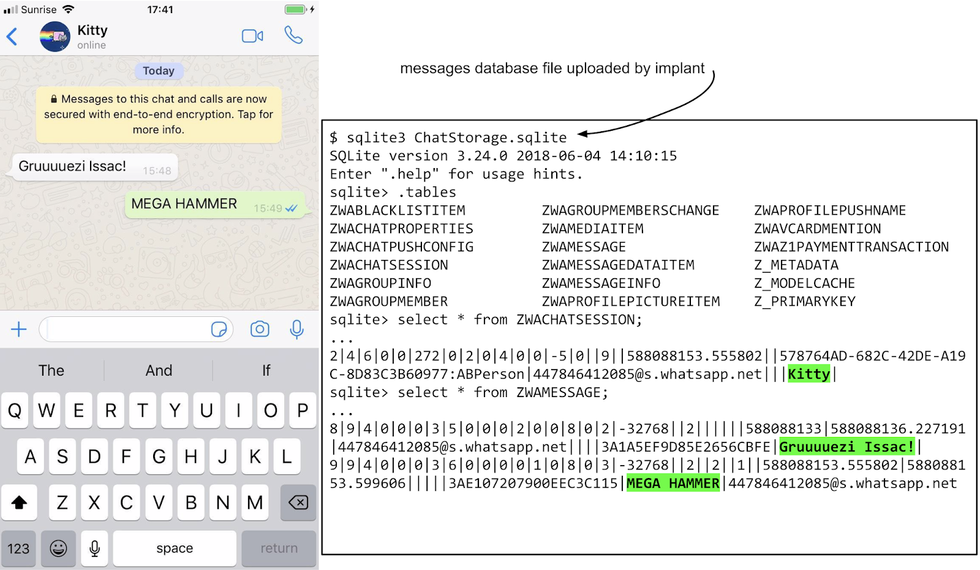
The malicious websites installed what the researchers have called a "monitoring implant" onto the iPhone. This implant was then able to access a large amount of personal data stored on the compromised devices, including the owner's contacts list, images in their camera roll, their real-time location, and their iMessage chat logs.
The implant accessed Apple's iMessage and chat logs made by encrypted messaging apps like WhatsApp and Telegram. Despite their encryption, the attackers could see the contents of these messages in plain text, as was also the case with the Gmail app.
The implant could also see the GPS location of the iPhone, as well as the Wi-Fi networks it had joined and their passwords.
Apple has said it does not wish to comment on the news.
Cybersecurity Ian Beer of Google's Project Zero research team said in a company blog post: "There was no target discrimination; simply visiting the hacked site was enough for the exploit server to attack your device and, if successful, install a monitoring implant. We estimate that these sites receive thousands of visitors per week."
The researchers believe the exploit was effective on "almost every version [of iPhone software] from iOS 10 through to the latest version of iOS 12."
Beer added: "Let's also keep in mind that this was a failure case for the attacker: for this one campaign that we've seen, there are almost certainly others that are yet to be seen."
Of the 12 separate security flaws exploited by the attackers, most were bugs in Safari, Apple's web browser installed by default on every one of the billion-plus iPhones sold to date. All models of iPhone were affected by this attack until they were updated by their user to iOS 12.1.4.
The researchers said that once the implant is installed on the victim's iPhone, the owner does not know that their handset has been compromised. Beer explained: "There is no visual indicator on the device that the implant is running. There's no way for a user on iOS to view a process listing, so the implant binary makes no attempt to hide its execution from the system."
Beer added that the implant "is primarily focused on stealing files and uploading live location data. The implant requests commands from a command and control server every 60 seconds."
Speaking further about the implant, Beer said: "The implant has access to almost all of the personal information available on the device, which it is able to upload, unencrypted, to the attacker's server."
One saving grace is that the implant is killed when the iPhone is switched off and rebooted. When switched back on, it is no longer active unless the user visits one of the malicious websites again. Beer concluded, "Given the breadth of information stolen, the attackers may nevertheless be able to maintain persistent access to various accounts and services by using the stolen authentication tokens from the keychain, even after they lose access to the device."
GearBrain Compatibility Find Engine
A pioneering recommendation platform where you can research,
discover, buy, and learn how to connect and optimize smart devices.
Join our community! Ask and answer questions about smart devices and save yours in My Gear.
